Reading time: 4 minutes
61% of insurance revenue flows through independent agents using devices carriers cannot see, manage, or protect.
For insurers, that makes securing independent agent devices one of the most urgent cybersecurity and compliance challenges in the business.
Carriers are fighting a two-front war. Distribution leaders need faster onboarding to grow premiums, while security leaders must satisfy NYDFS Part 500 and strict third-party access controls.
The result is a dangerous gap. Corporate offices run modern zero-trust architectures, yet the agents who generate most of the revenue still work from unmanaged laptops at kitchen tables and in truck cabs.
This extended enterprise is now the primary attack surface. Up to 60% of security incidents in insurance originate from third-party devices.
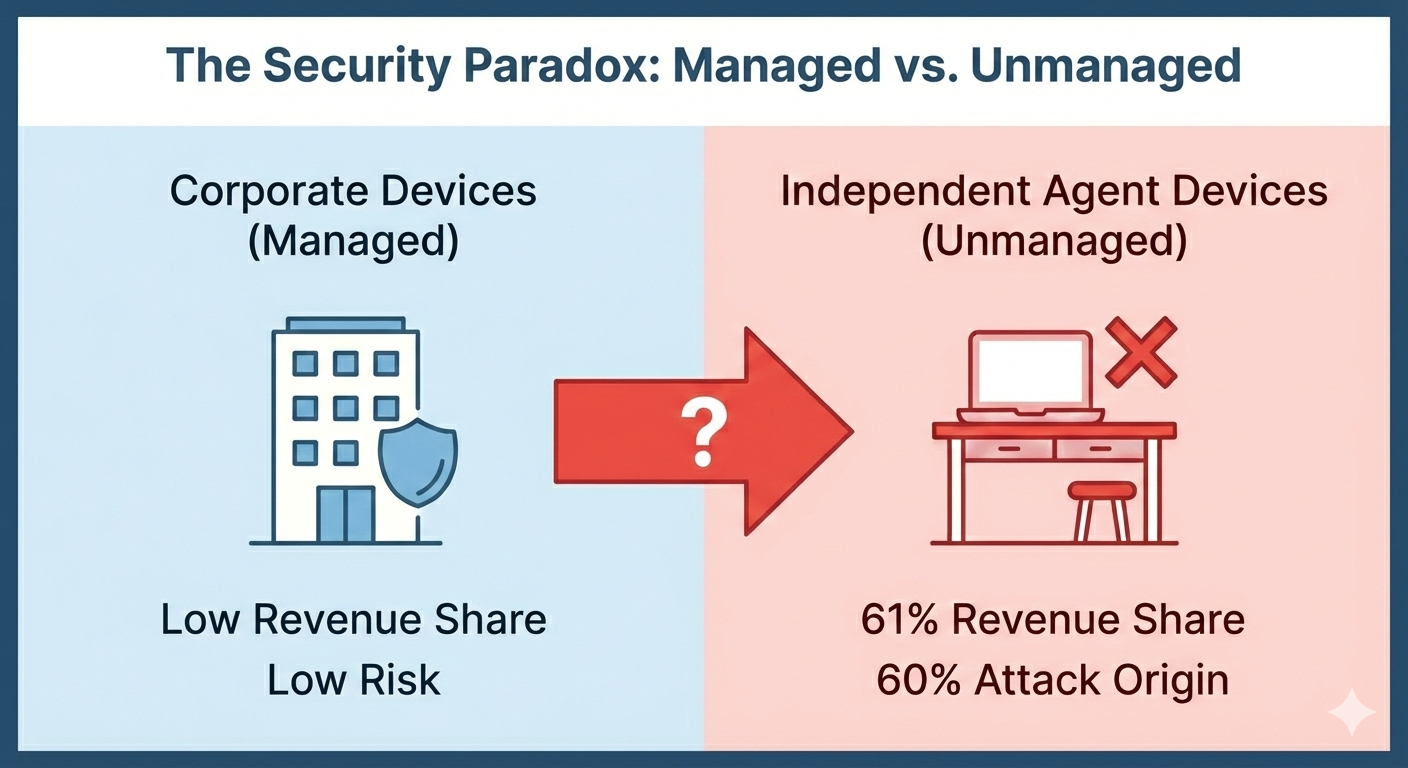
Most insurance revenue flows through unmanaged independent agent devices, which now represent the largest cybersecurity and ransomware risk surface.
But the industry is shifting. Carriers are moving from legacy VDI toward Continuous Device Trust to secure agents without slowing growth.
Key Takeaways for Insurance Leaders:
-
60% of attacks originate from unmanaged third-party devices
-
NYDFS 500.11 and NAIC 668 require technical verification, not contracts
-
Device Trust secures agents without MDM or VDI and cuts costs up to 80%
Rather talk to someone directly about your agent device risk?
Talk to a Device Trust Expert
Why Legacy Tools Fail to Secure Independent Agent Devices
The problem with securing the perimeter isn’t a lack of effort; it’s that legacy tools like Mobile Device Management (MDM) and Virtual Desktop Infrastructure (VDI) were never built for the independent agent model.
The MDM Privacy Barrier
Mobile Device Management (MDM) is the standard for corporate-owned devices, but it fails completely in the independent channel.
- Technical Impossibility:
- Agents appointed with 10–15 carriers cannot enroll one laptop into 10 different MDM systems.
- The “Big Brother” Problem:
- Agents refuse software that can wipe devices or track location.
- The Result:
- Carriers remain blind to device posture.
The “VDI Tax” on Profitability
Virtual Desktop Infrastructure (VDI) attempts to solve the privacy issue by streaming a remote desktop, keeping data off the endpoint.
However, it introduces what many now call the “VDI Tax”; A cumulative burden of high costs and technical friction.
- Prohibitive Cost (OpEx): VDI requires an annual overhead of $1,000–$1,500 per user. For a carrier with 10,000 agents, that is $10–$15 million in operating expenses without improving productivity.
- Workflow Destruction: In the field, VDI struggles with latency. Adjusters using specialized software (like Xactimate) find that VDI blocks local peripheral access, causing field productivity to drop 30–40%.
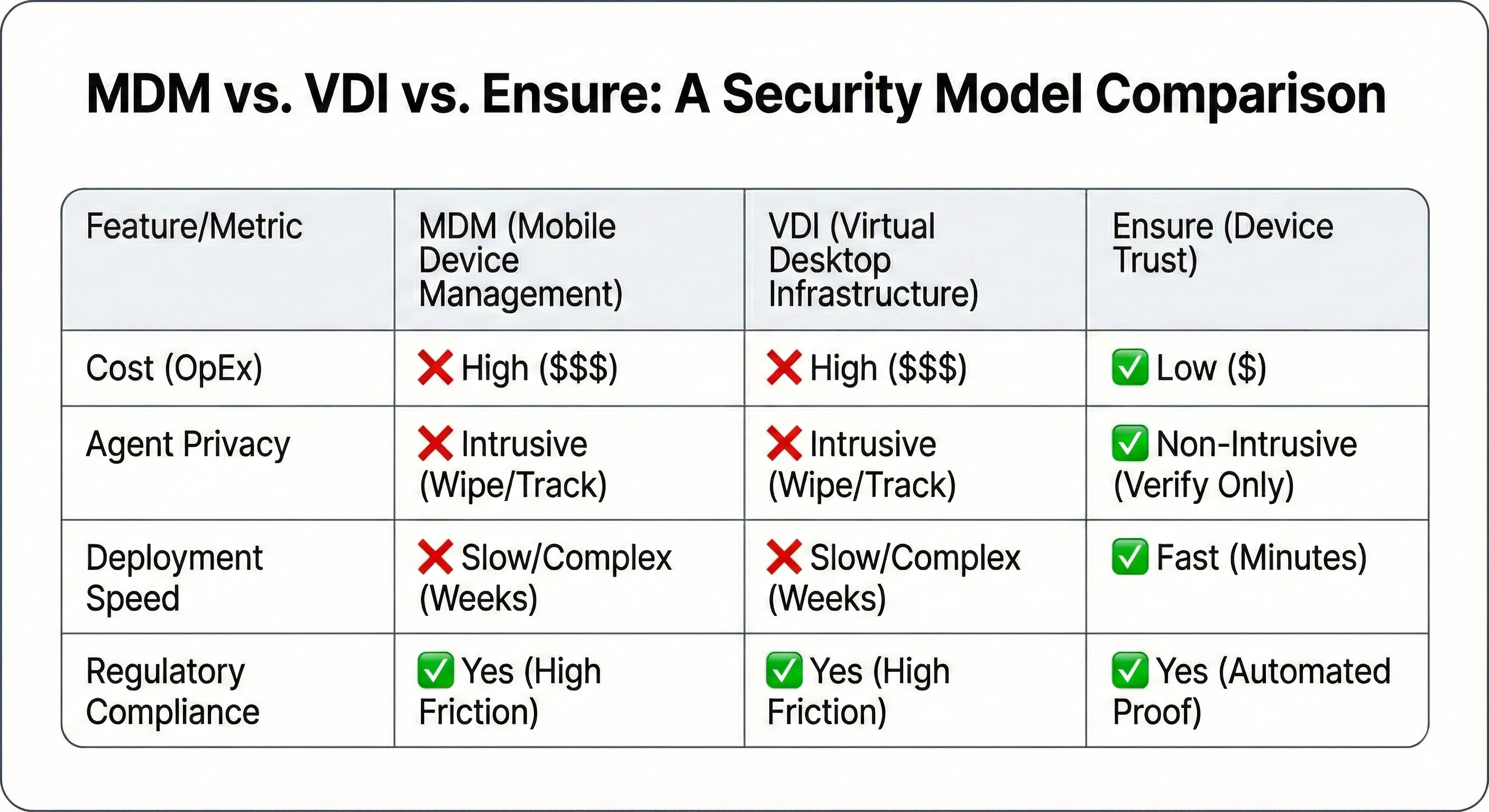
Continuous Device Trust gives carriers real-time visibility into every agent device without installing MDM or VDI.
Legacy tools make it harder, not easier, to secure independent agent devices at scale.
Still paying the VDI tax?
Get a Free Device Trust Assessment
Compliance Requirements for Securing Independent Producer Devices (NYDFS 500 & NAIC Model Law)
The regulatory landscape for Third-Party Risk Management (TPRM) shifted drastically in 2024–2025.
Insurance commissioners are no longer satisfied with “paper compliance.”
- NYDFS 500.11: Mandates continuous monitoring and real-time verification of third-party endpoints before data access.
- NAIC Model Law 668: Requires “periodic assessment” of third-party security posture and technical verification for licensees.
The Auditor’s Demand: CISOs must now prove that encryption is active, firewalls are on, and OS patching is current before any Non-Public Information (NPI) is accessed.
How to Secure Independent Producer Devices Without MDM or VDI
To secure the unmanaged workforce without the intrusion of MDM or the cost of VDI, modern carriers are adopting Lightweight Device Trust.
Ensure Endpoint closes the “Access-Trust Gap” by moving away from device ownership and toward a model of continuous verification.
Our platform secures every sign-in to every carrier portal, ensuring only healthy devices touch sensitive data.
1. Zero-Knowledge Verification
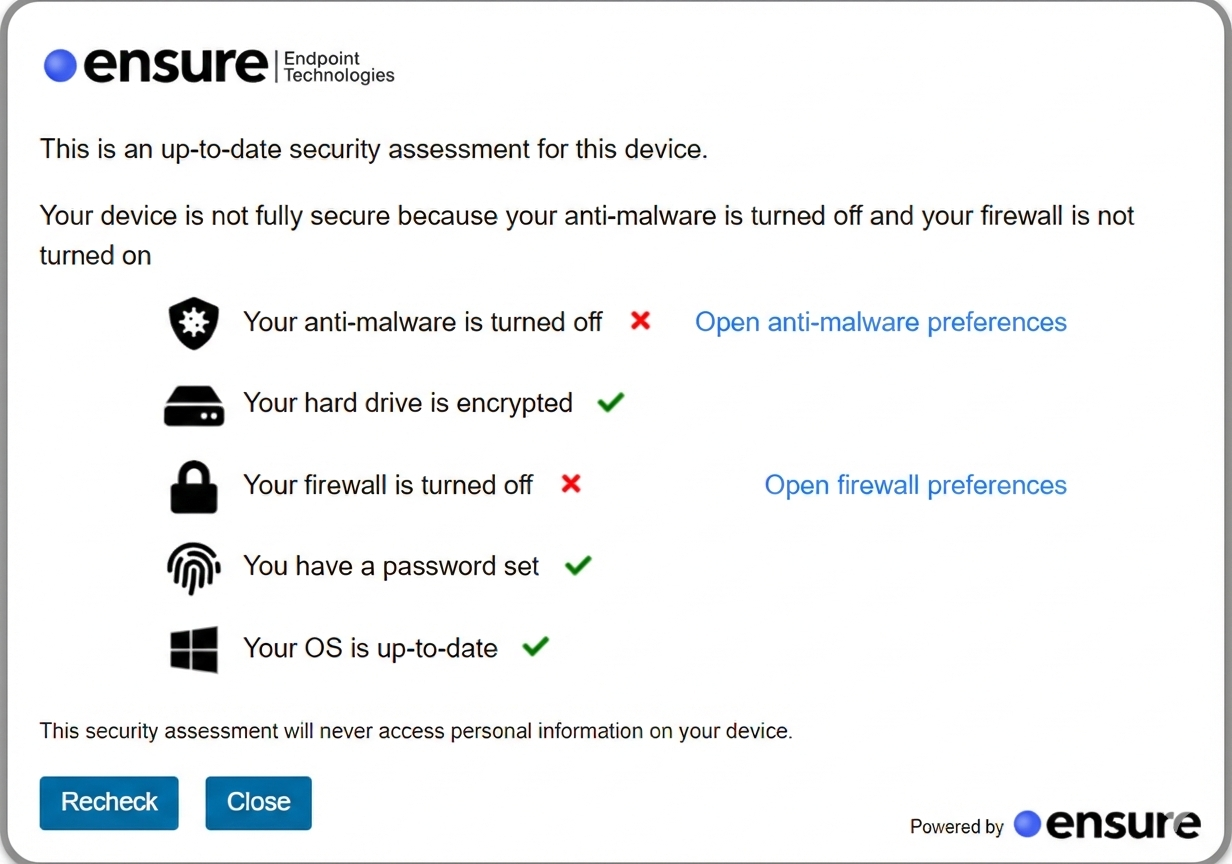
Agents fix security issues themselves in minutes, preserving productivity while maintaining compliance.
The first step in managing agent BYOD is gaining visibility without being intrusive.
Ensure provides an Automated Oversight Mechanism via a lightweight and privacy-centric app that verifies security posture at the exact moment of access.
Unlike MDM, Ensure never accesses personal information; it simply checks for essential “trust signals”:
- Anti-malware active
- Disk encryption (BitLocker/FileVault) enabled.
- Firewall status and OS update status.
2. Control Evidence and Audit Trails
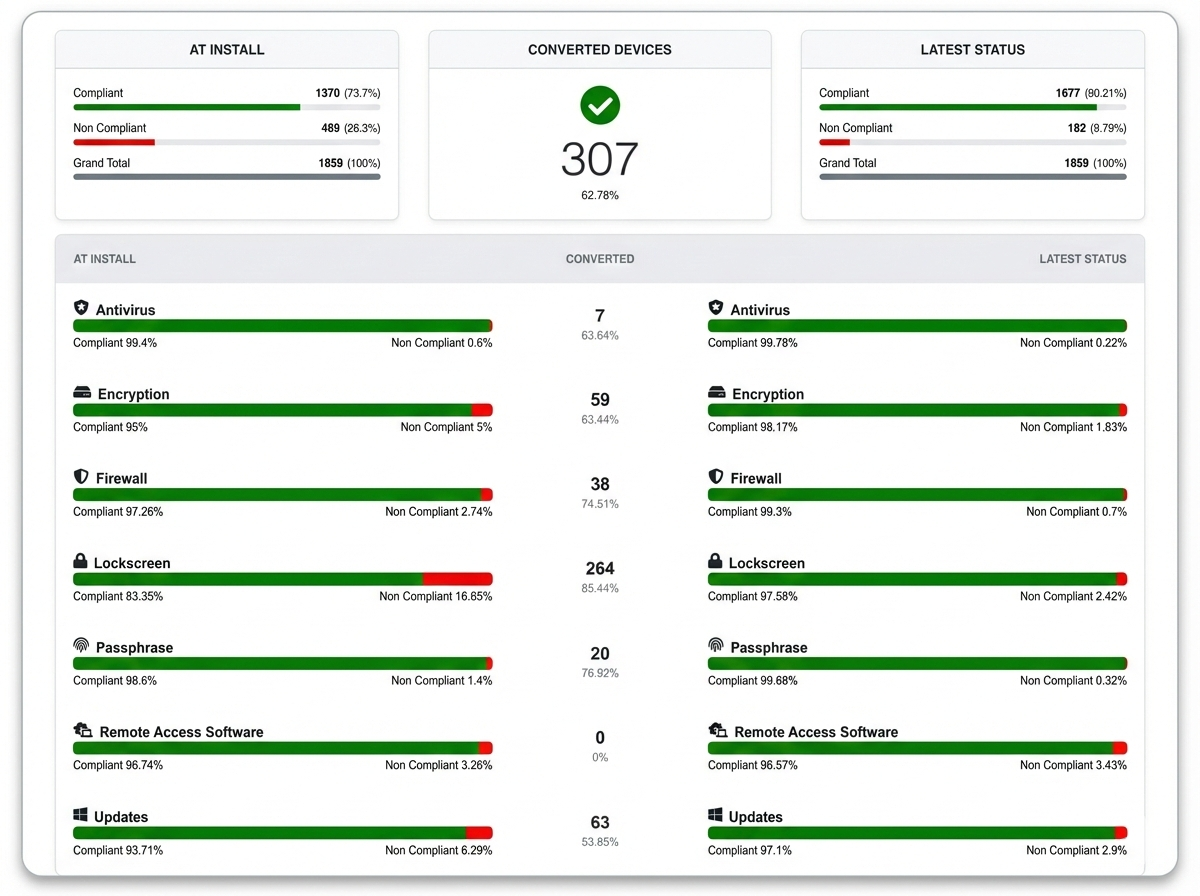
Ensure provides a real-time view of every third-party device accessing your portals.
Ensure generates Immutable Posture Logs for every session.
This provides the “Control Evidence” required by regulators to prove a device was secure at the time of login, transforming “trust” into verifiable “evidence.”
3. Agent Self-Remediation
Security shouldn’t slow down sales.
When a device fails a check, Ensure provides the user with clear, instant instructions to fix the issue.
Agents and brokers can resolve problems, like an outdated OS or disabled encryption, in minutes, preserving their independence while maintaining your security standards and eliminating Tier 1 support tickets.
Security as a Profit Center
Implementing Device Trust isn’t just a defensive move; it’s a financial lever to improve your Combined Ratio.
- Reduce Premiums: Modern cyber insurance underwriters (like Beazley and Aon) now explicitly ask if you verify third-party endpoint security. Carriers implementing Device Trust report a 15–20% reduction in cyber liability premiums.
- Scalable Growth: Enable “Zero-Touch Onboarding.” Verify new agents in minutes and scale your distribution footprint without the linear cost of hardware or VDI seats.
Your perimeter is no longer inside your office. It’s the laptop in an adjuster’s truck and the tablet on a broker’s kitchen table.
It’s time to continuously secure independent agent devices while respecting agent independence.
Ready to secure every agent device before login?
Talk to a Device Trust Expert

