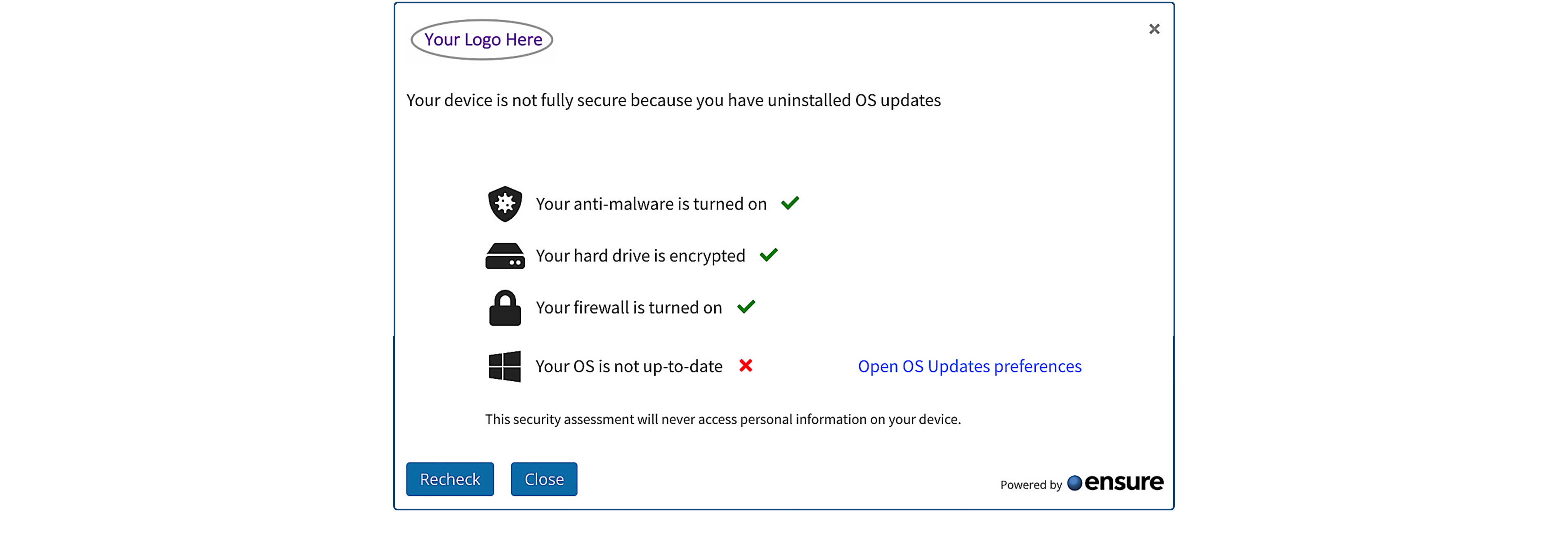
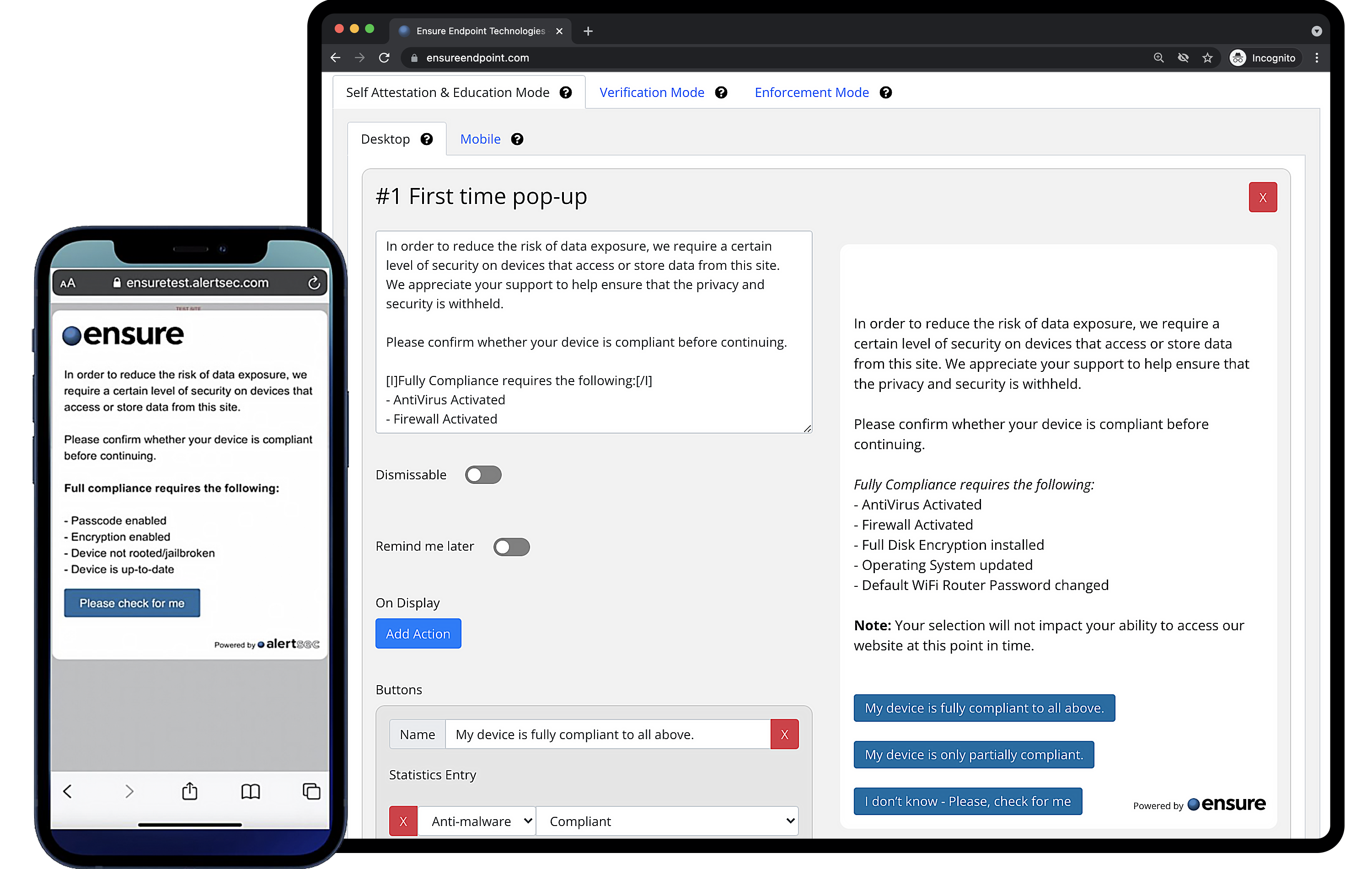
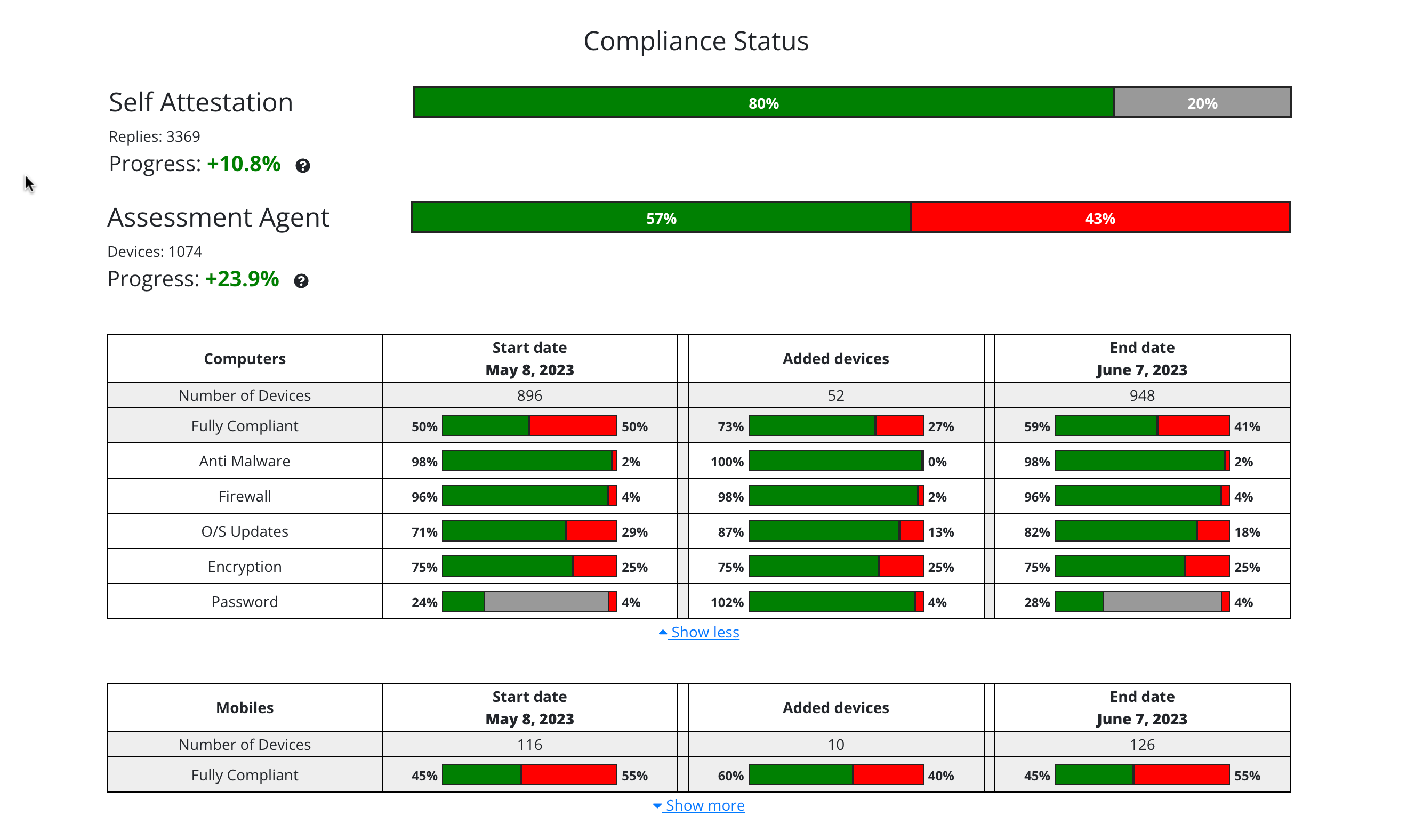
As authentication alone no longer guarantees security, organizations must also ensure that the devices accessing sensitive cloud services and enterprise data are compliant and trustworthy. This applies equally to employees, brokers, agents, vendors, and consultants operating in today’s hybrid workplace.
Device Trust Passport™ is the cornerstone of the Ensure compliance system — a proprietary technology that establishes verified trust between users, devices, and cloud services. It provides connection-control enforcement through continuous, real-time verification of device posture, determining whether an endpoint is authorized to access protected enterprise resources.
By ensuring that only compliant and trusted devices are allowed to connect, Device Trust Passport™ extends Zero Trust principles to the device layer, forming a vital part of modern regulatory compliance and secure access control.